Phishers Thrive in Free Tiers - A Case Study
- By Miloslav Homer
- Tue 17 September 2024
- Updated on Tue 17 September 2024
Analysis (a.k.a. The Facts)
Step 1: Email
The email is simple, and vaguely technical. A splash of color and a clear message:
Attention: victim@provider.tld
Authentication for victim@provider.tld is set to expire today 9/17/2024 7:18:10 a.m.
Access to the mailbox and documents will be limited after expiry, Maintain / Renew login key to continue using the mailbox.
Keep Password
Failure to complete request issues found on the system will no longer be investigated or fixed
cPanel on provider.tld
Let's follow the lead, we should be redirected to an ugly page...
Step 2: The form
The form is simple. One feature that stands out is a simple change based on the email address. Once you enter a full email address, javascript tries to get a logo for the company to show it to the victim in the form to build up trust. I like that - ineffective for us, but it's a nice touch.
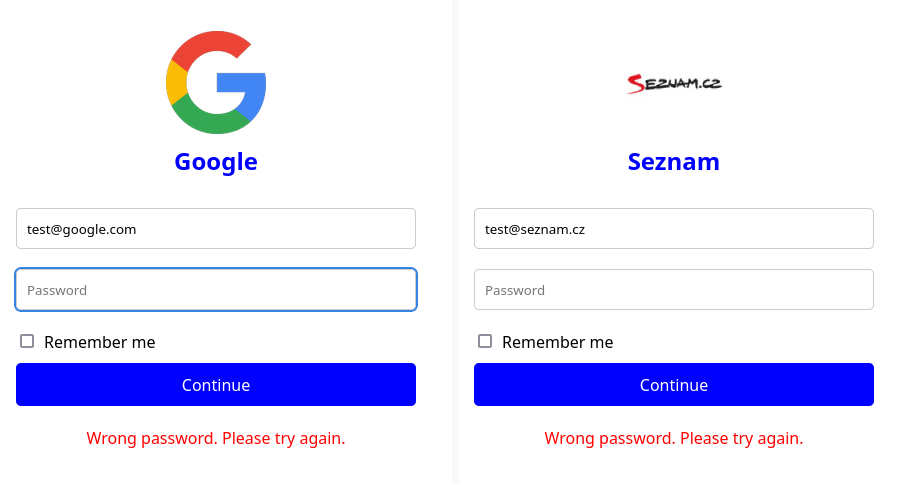
All you need to do is to get https://logo.clearbit.com/domain.tld, and in response you should get an image.
Another fantastic free service to use - no trace of credentials anywhere.
Oh, and any password is wrong - it is still being sent away though.
Step 3: Credentials Exfil
Another interesting bit - the phishers used a Telegram bot with hardcoded credentials. A simple POST request sends the credentials alongside an IP address to a private channel.
Interpretation (a.k.a. Opinions)
Telegram
Using Telegram has benefits - Telegram APIs are free of charge. Moreover, it's a well-known service that has legitimate uses. Therefore it's unlikely to be blocked, and it might even fly under the radar of detection software.
Taking a look at the metadata available (e.g. getMe method or message responses) gave me nothing, so I gave up.
Form infra
OORT is a decentralized, verifiable cloud computing platform. By utilizing global resources from data centers to smartphones, it aims to enable trustworthy AI applications for humanity.
Taking a look at the bug bounty part, I see they are only interested in issues in their special protocol. That's not their only product though - they have a solid hosting service offering too! Check out the free tier - you can host static sites for free.
I've reported the abuse of their services.
Email infra
It's easy to see the domain from which the attack came. Navigating there reveals a Zimbra installation.
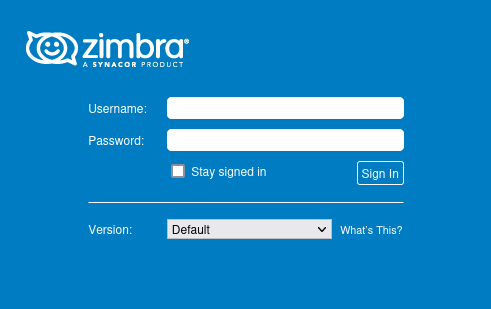
A few searches later, it seems that Zimbra had a couple of issues in the past. Then I correlated the info and navigated to this exploit on GitHub.
I didn't even run the exploit, all I did was look at whether the path mentioned in the expoit was on the server. It was and it's a JSP webshell.

That concludes the analysis of how the attackers sent the emails - compromising a server to misuse for this purpose.
Weak points
One of the hardest parts of these campaigns is sending emails. Spam filters are great, and there are more mechanisms to bypass, such as domain reputation. Even if you manage to get a full score at spam verificators such as mail-tester, you are not guaranteed that your email will arrive (see this article). I suspect that this is the least cost-efficient part of the attack.
Since the attackers used an exploited server on a domain, this will stop working any minute as their email domain reputation will plummet. Still, the overall plan is solid, and they might find other Zimbra instances with these vulnerabilities, so they don't need to invest in new research.
The message wording was weird, the pressure is kinda there, and losing access is never good. And cPanel is a thing. I don't think they did their homework, it completely missed the mark here. It looked okayish.
The form tried to look professional by displaying a logo of the company from the domain, I'll give props for that. But it was clunky. The overall flow was fairly quick though, and the "wrong password" message prompts a desperate user to try their common passwords.
5/10, try to target/profile your victims better.
Conclusion
This was another phishing attack with minimal investment.
- Emails: free, by the virtue of using a public exploit.
- Forms: free, by abusing a free tier of a service provider. Sprinkle another free service to show the victim's logo.
- Data exfil: free, by abusing a legitimate messaging service with benevolent API.
The attack still missed the mark, as it was clunky and unrelated to our stack. Too bad, try again next time.
